The open source tool Open Policy Agent is used for the central management and enforcement of policies in distributed systems. It allows policies to be defined as code and flexibly applied to use cases such as API authorization, cloud security, and Kubernetes governance. By decoupling policy from application logic, the tool provides a scalable solution for access control and security checks.
At a time when more and more aspects of IT infrastructure are being treated as code, policy management is also playing a crucial role. Policy as Code (PaC) is an approach in which policies and rules are recorded in machine-readable code. These policies define aspects such as security, compliance, and governance in a system or IT infrastructure and are treated similarly to software, meaning they can be versioned, tested, and rolled out automatically through CI/CD pipelines. Infrastructure as Code (IaC) and PaC have many similarities, as both approaches aim to replace manual processes with automatable, versionable, and verifiable configurations. This approach to consistent and repeatable deployment reduces human error and makes it easier to manage complex environments [1].
The introduction of Policy as Code offers significant advantages in the management and implementation of security and governance policies. By defining them in code, they can be managed, reviewed, and deployed in versioning systems such as Git. This minimizes human error and manual intervention that can occur with traditional policy management. By automating policies, companies can respond more quickly to changes in the IT environment, requirements, or even security threats [2].
It is important that changes are consistent and reproducible across all environments. Even when resources are dynamically adjusted or scaled, PaC ensures that policies are automatically transferred to each new instance, virtually eliminating policy drift. In practice, such deviations often lead to security gaps or other critical operational problems. Code versioning also enables complete traceability of changes, allowing companies to ensure that every policy adjustment is documented and traceable.
The systematic and automated implementation of security policies greatly reduces the risk of misconfigurations or security breaches. The definition of policies can be integrated directly into the development process, enabling proactive enforcement of security requirements [2]. Instead of fixing potential security vulnerabilities after the fact, developers can work with secure, predefined policies from the outset. This approach supports the shift-left strategy, in which security aspects are incorporated early in the development process [3].
Policies and their enforcement
A policy is a binding rule or guideline that defines clear conditions and specifications for controlling and managing access to systems, data, or resources. It specifies which actions are permitted or prohibited under which conditions and how processes in a system should be designed [4]. A policy engine is used to enforce policies. This is a software component or system that defines, manages, and enforces guidelines in a specific context. To map these requirements, a policy engine consists of several components, each of which performs different tasks. Policies can be used in various areas to determine who can access sensitive data, which network requests are allowed or blocked, and which users can access certain cloud resources. Their use ensures consistent compliance with defined rules, thereby strengthening security and compliance in complex IT environments [2], [5].
Policy: Definition, evaluation, and enforcement
Suitable tools and methods must be provided to enable policies to be defined and managed flexibly. A simple example of this could be: “If user X wants to connect to resource Y, check whether they have the necessary permissions.”
However, such rules do not have to be static; they can also be formulated as dynamic rules. An example of a dynamic rule would be: “Employees may only access the database if they are on the company network and access takes place during their defined working hours.”
In this step, the engine checks the defined rules against the current context. In other words, every time an action or event occurs that is associated with a policy, the policy engine must decide whether the action is allowed or must be blocked.
After the decision has been made, the engine implements it by executing allowed actions and blocking unauthorized ones.
To ensure that security-related events are immediately known, notifications can be sent to administrators or specified security teams on request.
Advantages
Manual policies are often inefficient, error-prone, and difficult to scale. The lack of automation and consistency increases security risks and workload. A policy engine is therefore a versatile tool that enables organizations to consistently enforce and automate their policies and rules. Whether in IT security, network management, cloud management, or compliance, a policy engine ensures that processes run efficiently, securely, and in compliance with regulations. This enables companies to ensure that all actions in the system remain transparent, controllable, and traceable [2].
Make APIs secure!
Explore the API Security Track
Open Policy Agent
Now that we have looked at the concept of policy as code (box: “Policies and their enforcement”) and the basic functions of policy engines, the question arises: How can a flexible, scalable, and customizable solution be implemented that meets the diverse requirements of modern IT environments? This is where the Open Policy Agent (OPA) comes into play.
Open Policy Agent is an open-source tool that provides a powerful and flexible solution for managing and enforcing policies in modern IT environments. It serves as a central policy engine capable of making real-time decisions about access rights and rule compliance. With OPA, policies can be consistently defined as Policy as Code and applied across different systems such as Kubernetes, microservices, API gateways, or CI/CD pipelines [6].
The tool uses the declarative language Rego to define complex rules and access conditions in a precise and traceable manner. These rules are formulated as code and evaluated directly by OPA to decide whether certain actions are permitted or not. OPA is often integrated into IT infrastructures to automate policy and access decisions, enabling centralized management and flexible adaptation of rules without having to modify individual systems directly. As a decision service, the Open Policy Agent provides a JSON response on request that specifies exactly whether a user is granted access to a particular resource or not.
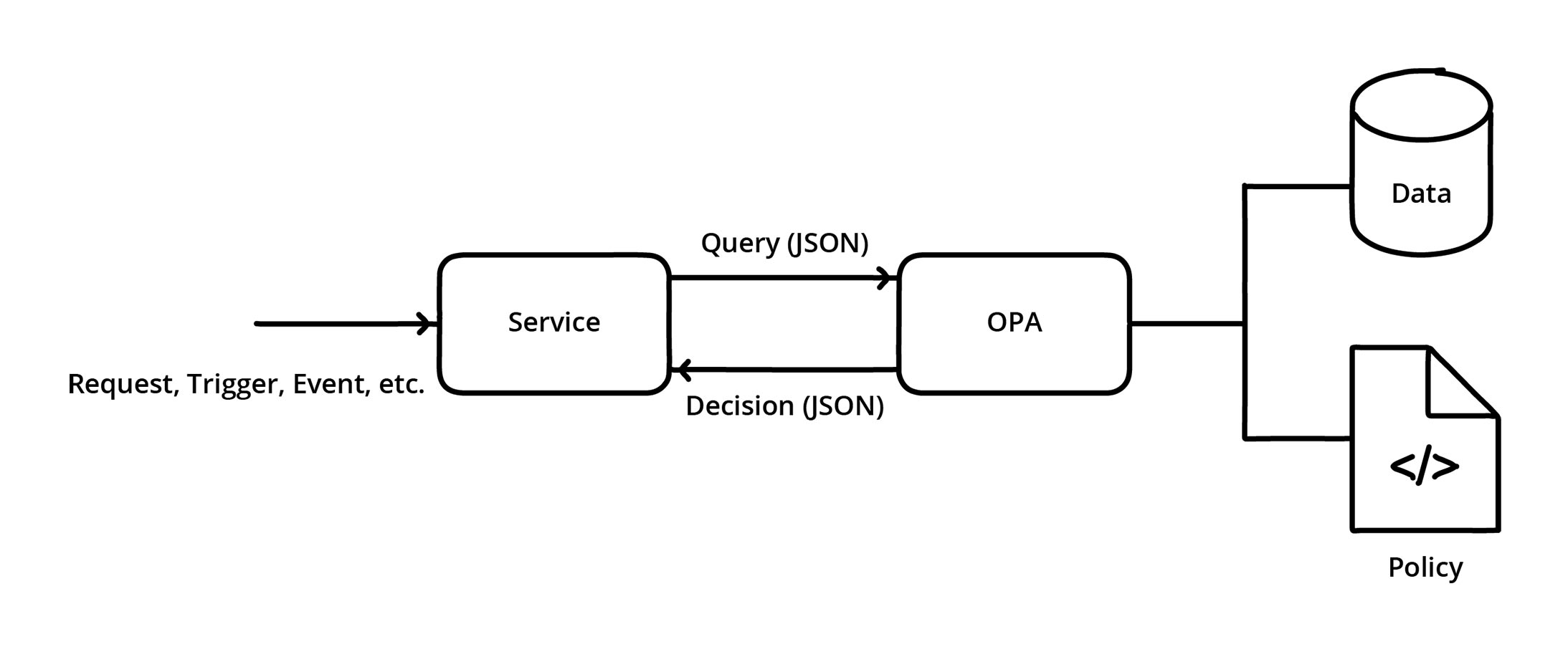 Fig. 1: Decision-making with the Open Policy Agent
Fig. 1: Decision-making with the Open Policy Agent
Authorization policies are a special type of policy designed to separate the decision-making logic for access from the core logic of the service. A service—such as a microservice, API gateway, or other component—sends a request to OPA. This request is transmitted as a JSON document and contains all the necessary information and context for evaluating the policy. OPA then evaluates the request based on predefined policies written in Rego.
These policies are designed to evaluate various conditions, such as user roles, resource attributes, etc., and are stored together with data used in policy evaluation. Policies define the rules that control access, and the data provides the additional context needed for decision-making. For example, the policy could define who is allowed to access certain resources, and the data could contain information about users and resources. OPA returns a decision (in JSON format) to the service. This decision can be simple, such as “allow” or “deny,” or it can contain detailed information about why a decision was made [6] (Listing 1).
Listing 1: Example policy in Rego
package authz
import rego.v1
# Die Regel erlaubt den Zugriff nur, wenn der Benutzer die Rolle "admin" hat
# und der API-Endpoint "/admin/dashboard" aufgerufen wird.
default allow := false
allow if {
input.user.role == "admin"
input.request.path == "/admin/dashboard"
}
Due to its architecture, OPA is often used to enforce policies in distributed systems and cloud environments [7]:
- Kubernetes Admission Control: Here, policies are defined to ensure that certain requirements for the cluster are met, such as prohibiting root privileges for containers or restricting them to approved images.
- API access control: Authorization rules are often defined here to determine who is allowed to access certain endpoints or which actions are permitted.
- CI/CD pipeline compliance: This ensures that only verified or approved changes are deployed. For example, if it is ensured that all configurations comply with certain security standards, approval can be granted.
- IAM: This enables flexible, centralized, and fine-grained management of access controls.
- Database security: This allows access to sensitive data to be controlled. For example, rules can be defined to determine who has read and write access to specific data records.
- Network access control: Rules for network access can be defined and enforced not only in cloud environments but also in on-premise networks. For example, access to certain ports and services can be restricted.
- IaC policy checking: OPA can be used here to check IaC templates. With appropriately defined policies, you can ensure that infrastructure elements comply with company guidelines before they are deployed.
- Service mesh policy enforcement: Similar to network access control, policies can be used here to ensure that only certain services are allowed to communicate with each other at the network level.
Policy engine vs. business rule engine
“Why do you actually need two systems to manage rules? Isn’t one enough?” This question quickly arises when you come across the terms policy engine and business rule engine. Both systems seem to perform similar tasks, but their focus and application differ fundamentally.
A business rule engine (BRE) is a software system or component that manages and enforces business rules in a dynamic, automated manner. Business rules are predefined instructions or criteria that determine how a company makes decisions or executes processes in specific situations. The BRE separates these rules from the underlying application logic, enabling flexibility and adaptability without the need to change the code [8], [9].
It can therefore be said that both systems automate decision-making processes in software and IT systems and enforce certain rules or guidelines. But when should which engine be used?
Policy engines are typically used in security-critical or compliance-oriented areas, for example to enforce security policies, comply with data protection regulations, or manage access rights.
They are also used in IT security infrastructures such as firewalls, authentication, and authorization systems. The centralized policies are often highly abstract and describe strategic guidelines. They regulate at a higher level how and when certain measures are to be carried out and can help to comply with legal or internal requirements [5]: “Only users with the role ‘manager’ or ‘administrator’ may access sensitive financial data.”
Business rule engines, on the other hand, are typically used in applications or systems that require dynamic adjustments to business logic. This applies, for example, to financial systems, insurance, or commerce applications in which business decisions such as pricing, approval procedures, credit granting, or discount calculations are automated. They offer a high degree of flexibility and agility, as changes to the business process can be made without adjusting the program code. The business rules are detailed and specific, with a clear focus on the automation of business processes and decisions [9]: “If the order value exceeds $100, grant a 10 percent discount.”
| Criterion | Policy Engine | Business Rule Engine |
|---|---|---|
| Purpose | Enforcement or automation of guidelines and strategic requirements | Automation of business logic and decisions |
| Area of application | IT security, compliance, governance | Business processes, e.g., pricing, approvals |
| Level of abstraction | Higher, strategic level | Operational, fine-grained level |
| Guideline vs. rules | Guidelines are based on strategic requirements | Business rules are based on operational requirements |
| Flexibility | Changes often require formal reviews | Rules can often be changed directly by specialist departments |
Table 1: Policy Engine and Business Rule Engine profiles
Despite their differences, there are also numerous similarities. Both systems aim to automate decision-making processes based on predefined rules or guidelines and are designed to replace or support human decisions in certain scenarios. To do this, both use a central collection of rules and guidelines that are explicitly defined and serve as the basis for system behavior. By changing these, the system behavior can be adapted and modified accordingly. This flexibility ensures that new requirements can be responded to without changing the entire application code. The decision logic is therefore separated from the actual application or system. This ensures that the rules and guidelines can be maintained independently of the application.
| Similarities | Policy Engine | Business Rule Engine |
|---|---|---|
| Automation of decisions | Guideline decisions | Business decisions |
| Rule-based control | Guidelines as a basis | Business rules as a basis |
| Adaptability | Adaptation of policies to changing requirements | Adaptation of rules based on new business requirements |
| Separation of logic and execution | Guidelines are separated from the application code | Business rules are separated from the application code |
| Goals are consistency & efficiency | Ensuring consistent policy application | Ensuring consistent business decisions |
| Centralized management | Policies | Business rules |
Table 2: Similarities between policy engines and business rule engines
In summary, it can be said that a policy engine operates at a more strategic and security-oriented level, while a business rule engine focuses more on the operational implementation of business processes.
STAY TUNED!
Learn more about API Conference
Conclusion
Open Policy Agent is an effective solution for managing policies and access controls in a wide range of applications and systems. Its flexible architecture and use of declarative policies enable precise and granular control of access rights, meeting the requirements of modern enterprises. The tool can be used both as a central component in conjunction with an API gateway in distributed environments and for detailed control of individual applications.
However, the associated challenges must be taken into account. The diversity of applications and systems, as well as the dynamic nature of enterprise environments and possible use cases, pose significant challenges that must be addressed when implementing OPA.
In the next parts of this series, we will delve deeper into the details and look at productive use, testability, integration into CI/CD pipelines, and scenarios in the cloud and in distributed architectures. So stay tuned!
Links & Literature
[1] Ray, Jimmy: “Policy as Code”; O’Reilly Media, 2024
[2] “Introduction to policy as code with automation”: https://www.redhat.com/en/blog/policy-as-code-automation
[3] “Shift Left Security in Practice”: https://www.tigera.io/learn/guides/devsecops/shift-left-security/
[4] “Guide to Attribute Based Access Control (ABAC) Definition and Considerations”: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-162.pdf
[5] “What Is a Policy Engine”: https://www.strongdm.com/what-is/policy-engine
[6] “Open Policy Agent”: https://www.openpolicyagent.org
[7] “Introducing Policy As Code – The Open Policy Agent (OPA)”: https://www.cncf.io/blog/2020/08/13/introducing-policy-as-code-the-open-policy-agent-opa/
[8] “Business Rule Engines (BRE)”: https://www.gartner.com/en/information-technology/glossary/bre-software
[9] “Business Rules Engine (BRE): What It Is and How It Works?”: https://geekflare.com/business-rules-engine/
